'All wifi networks' are vulnerable to hacking, security expert discovers WPA2 protocol used by vast majority of wifi connections has been broken by Belgian researchers, highlighting potential for.
Microsoft says this about the KB893357 patch.
'In order to take advantage of WPA2, users will also need a wireless
LAN that includes the new standard and a Wi-Fi network adapter with the
processing power to handle AES encryption, Athwal says.
Many of the wireless LAN access points and client adapters being sold
today can use WPA2 and come with add-on software for client devices.'
So the question is, which adapters have the 'processing power'? Most
if not all adapters on the shelf say they support WPA security. But
that isn't true if one is looking for AES support. I installed this
patch and then installed the Netgear WG511v2 PCMCIA adapter and the
best I could get was TKIP while my router WRT54Gv3 supports both TKIP
and AES.
So what is the change this patch suppose to bring? Is it to replace
WPA drivers shipped with WPA capable cards?
Windows Xp Wpa2 Patch
Microsoft today revealed that it quietly patched Windows last week against vulnerabilities in the Wi-Fi Protected Access II (WPA2) protocol used to secure wireless networks.
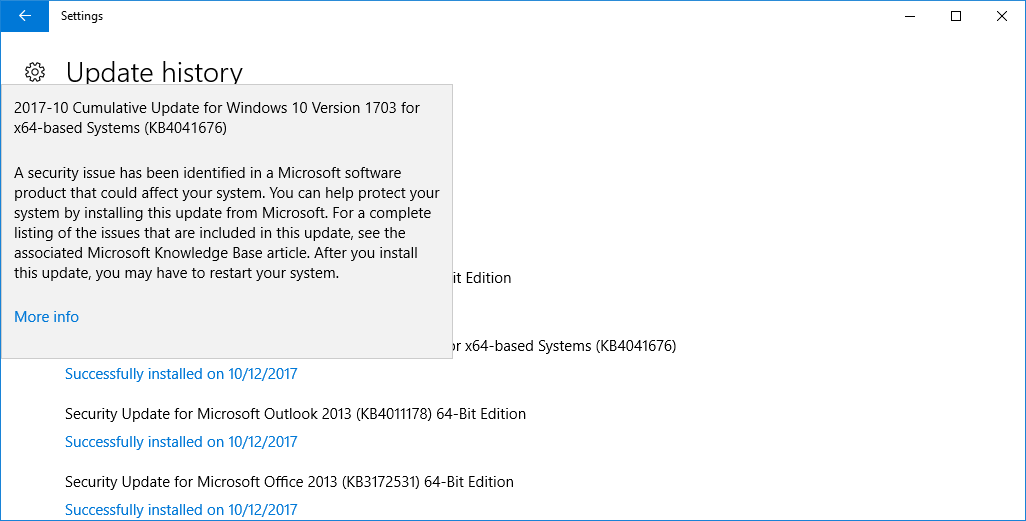
Details of the security update were only published Monday to Microsoft's Security Update Guide, the catalog-like portal that earlier this year replaced the decades-old practice of delivering explanatory bulletins.
All supported versions of Windows received the update, according to the catalog listing, including Windows 7, Windows 8.1, Windows 10, Windows Server 2008, Windows Server 2012 and Windows Server 2016.
The vulnerabilities were revealed today by Mathy Vanhoef, a researcher at Katholieke Universiteit Leuven in Belgium. On a website that went live Monday, Vanhoef said that weaknesses in WPA2 allowed criminals to read information transmitted over a Wi-Fi network thought to be encrypted by the protocol.
'Attackers can use this novel attack technique to read information that was previously assumed to be safely encrypted,' Vanhoef wrote on the site. 'This can be abused to steal sensitive information such as credit card numbers, passwords, chat messages, emails, photos, and so on.'
Vanhoef dubbed the attack 'Krack,' for 'Key Reinstallation Attacks.'
Windows Wpa2 Patch Download
Microsoft included the anti-Krack update in its October security slate released on Oct. 10, but the company held the news until today because information about Krack was scheduled to be issued this morning by Vanhoef, numerous security organizations and multiple vendors. 'In partnership with the International Consortium for Advancement of Cybersecurity on the Internet (ICASI), Microsoft participated in a multi-vendor coordinated disclosure to acknowledge and describe several Wi-Fi Protected Access (WPA) vulnerabilities,' Microsoft said in its update description.
The Windows security updates patched the client and server flavors of Microsoft's OS, but even then, users may be at risk, the firm warned. 'When affected Windows-based systems enter a connected standby mode in low-power situations, the vulnerable functionality may be offloaded to installed Wi-Fi hardware,' Microsoft said. 'To fully address potential vulnerabilities, you are also encouraged to contact your Wi-Fi hardware vendor to obtain updated device drivers.'
Windows PCs with Automatic Updates enabled have probably received the patches by this point. Managed devices must get the green light from IT personnel, as usual.

Vanhoef and Frank Piessens, another security researcher at Katholieke Universiteit Leuven, will present a paper on Krack Nov. 1 at a conference in Dallas, Texas. The paper can be found here.